Abstract: SQL Data breaches are a growing concern for individuals, organizations, and governments worldwide. A data breach refers to a security incident where sensitive or confidential information is accessed, disclosed, or stolen by an unauthorized person or entity. In this research paper, we examine the causes and consequences of data breaches, along with coding examples on how they happen. We also discuss prevention techniques that can be implemented to mitigate the risks of data breaches. The study utilizes primary and secondary data sources to explore these topics, including relevant literature, case studies, and statistical data. The findings suggest that data breaches are caused by a combination of technical vulnerabilities, human errors, and malicious attacks. The consequences of data breaches can be severe, including financial losses, reputational damage, and legal liabilities. To prevent data breaches, organizations should implement comprehensive security measures, including encryption, firewalls, access controls, and employee training programs.
What is a SQL Database?: A SQL database is a type of relational database management system (RDBMS) that is designed to store and manage data using the Structured Query Language (SQL). SQL is a programming language that is used to manage relational databases and perform operations such as inserting, updating, deleting, and querying data.
A SQL database consists of one or more tables that are used to store data in a structured format. Each table consists of one or more columns and rows. Columns represent the attributes of the data, while rows represent individual instances of the data.
SQL databases are used in a wide range of applications, from small-scale applications such as personal websites and blogs to large-scale enterprise applications. They are particularly well-suited to applications that require complex data relationships, such as e-commerce websites, financial applications, and content management systems.
One of the key advantages of SQL databases is that they provide a high level of data integrity and consistency. This is achieved through the use of constraints such as primary keys, foreign keys, and unique keys. Primary keys are used to uniquely identify each row in a table, while foreign keys are used to establish relationships between tables. Unique keys are used to ensure that no two rows in a table have the same values for a particular set of columns.
Another advantage of SQL databases is that they provide a high level of scalability and performance. They are designed to handle large volumes of data and can be easily scaled up or down to meet changing requirements. They also provide high levels of concurrency, allowing multiple users to access and modify the same data simultaneously without conflicts.
There are several popular SQL database management systems available, including MySQL, Oracle Database, Microsoft SQL Server, PostgreSQL, and SQLite. Each of these systems has its own strengths and weaknesses, and the choice of system will depend on the specific requirements of the application.
In summary, a SQL database is a powerful tool for storing and managing data in a structured and consistent way. SQL databases provide a high level of data integrity, scalability, and performance, making them well-suited to a wide range of applications. With the increasing importance of data in today’s digital age, SQL databases are likely to remain a key technology for many years to come.
What is a SQL Data Breach? A SQL data breach is an event in which an unauthorized person gains access to sensitive or confidential information, such as personal data, financial information, or intellectual property. Data breaches can be caused by a variety of factors, including software vulnerabilities, weak passwords, and social engineering attacks. In this paper, we will explore the different types of data breaches, how they happen, and how to prevent them in the context of MySQL and Oracle SQL databases.
Types of Data Breaches
There are many types of data breaches, including:
- Insider attacks: where an authorized person intentionally or accidentally leaks sensitive information.
- Malware attacks: where malicious software is installed on a computer or network to steal information.
- Social engineering attacks: where an attacker uses deception to obtain sensitive information from an individual or organization.
- Physical theft: where a physical device such as a laptop or USB drive containing sensitive information is stolen.
- Web application attacks: where an attacker exploits vulnerabilities in a web application to gain access to sensitive data.
Causes of Data Breaches: Data breaches can be caused by a combination of technical vulnerabilities, human errors, and malicious attacks. Technical vulnerabilities refer to weaknesses in computer systems, software, or networks that can be exploited by hackers. Examples of technical vulnerabilities include unpatched software, weak passwords, and outdated security protocols. Human errors, on the other hand, are mistakes made by employees or users that can lead to data breaches. Examples of human errors include lost or stolen devices, accidental disclosures, and social engineering attacks. Malicious attacks refer to intentional efforts by hackers or cybercriminals to gain unauthorized access to systems or data. Examples of malicious attacks include phishing, malware, and ransomware.
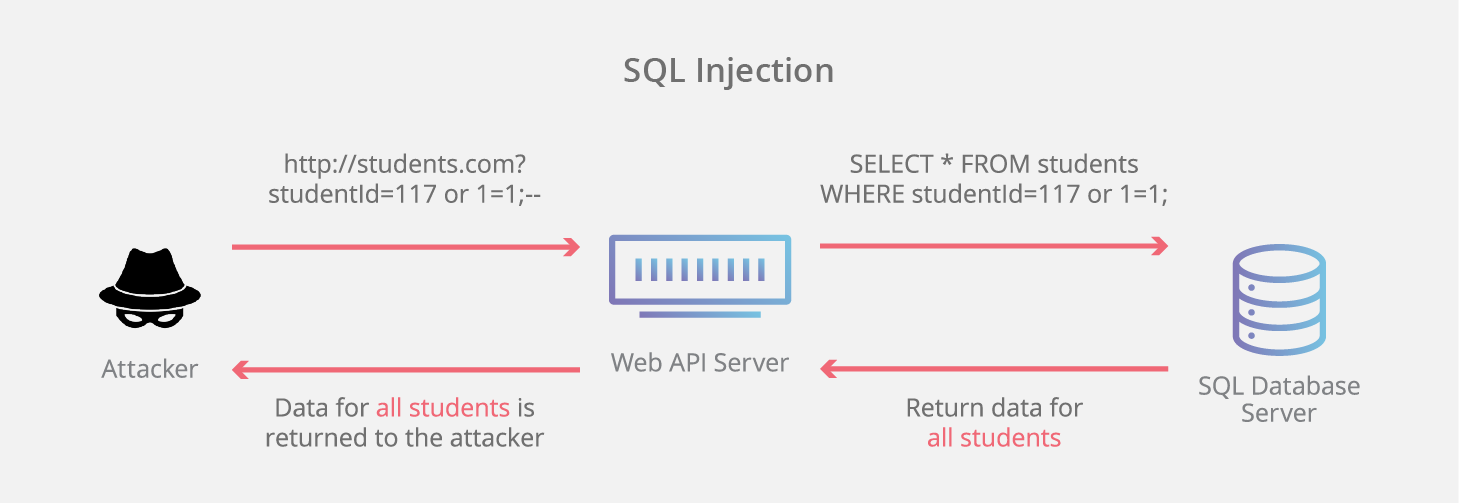
Coding Examples of How Data Breaches Happen: Data breaches can happen in several ways, and coding is often involved in these processes. One common method is through SQL injection attacks, which involve inserting malicious code into a website’s input fields to gain access to the underlying database. Another method is through cross-site scripting (XSS) attacks, which involve injecting malicious code into a website’s user interface to steal user data or credentials. A third method is through buffer overflow attacks, which involve exploiting a vulnerability in a program’s memory buffer to gain unauthorized access to the system. These are just a few examples of how coding can be used to facilitate data breaches.
Consequences of Data Breaches: The consequences of data breaches can be severe, both for individuals and organizations. For individuals, data breaches can lead to identity theft, financial fraud, and other forms of cybercrime. For organizations, data breaches can result in financial losses, reputational damage, and legal liabilities. In some cases, data breaches can lead to regulatory fines and sanctions. For example, the General Data Protection Regulation (GDPR) in Europe imposes fines of up to 4% of a company’s global annual revenue for data breaches.
Prevention Techniques: To prevent data breaches, organizations should implement comprehensive security measures that address technical vulnerabilities, human errors, and malicious attacks. Examples of prevention techniques include encryption, firewalls, access controls, and employee training programs. Encryption involves scrambling data so that it can only be read by authorized parties with the proper decryption key. Firewalls are network security systems that control incoming and outgoing traffic based on predetermined rules. Access controls involve restricting access to sensitive data and systems based on user roles and permissions. Employee training programs help educate employees on the risks of data breaches and how to avoid them. These prevention techniques should be implemented in a layered approach, where multiple security measures are used to protect against different types of attacks.
Preventing data breaches in MySQL and Oracle SQL databases requires a multi-layered approach that includes both technical and administrative controls. Some key strategies for preventing data breaches in MySQL and Oracle SQL databases include:
- Using secure coding practices: Developers should use prepared statements and parameterized queries to prevent SQL injection attacks in MySQL and Oracle SQL. Additionally, they should sanitize user input and validate data before inserting it into the database.
- Implementing strong password policies: Users should be required to use strong passwords that are difficult to guess or crack. Passwords should also be changed regularly and never reused.
- Patching software regularly: MySQL and Oracle SQL databases should be kept up to date with the latest security patches to prevent known vulnerabilities from being exploited.
- Configuring databases securely: MySQL and Oracle SQL databases should be configured securely, with access controls, encryption, and other security features enabled.
- Monitoring databases for unusual activity: Administrators should monitor MySQL and Oracle SQL databases for unusual activity, such as login attempts from unknown IP addresses or suspicious queries.
1st PHP Example of Preventing SQL Injections:
<?php
// Create a new PDO object to connect to the database
$pdo = new PDO('mysql:host=localhost;dbname=mydatabase', 'myusername', 'mypassword');
// Prepare a SQL statement with placeholders for parameters
$stmt = $pdo->prepare('SELECT * FROM users WHERE username = :username AND password = :password');
// Bind the parameters to their respective placeholders
$stmt->bindParam(':username', $username);
$stmt->bindParam(':password', $password);
// Set the parameter values from user input (in this case, from a form submission)
$username = $_POST['username'];
$password = $_POST['password'];
// Execute the statement
$stmt->execute();
// Fetch the results
$results = $stmt->fetchAll();
// Do something with the results (in this case, just print them out)
print_r($results);
?>In this example, we’re using PDO (PHP Data Objects) to connect to a MySQL database. We then use the prepare() method to create a prepared statement with placeholders for the parameters we’ll be using. The bindParam() method is used to bind the actual values to the placeholders.
By using prepared statements and parameterized queries, we can ensure that any user input is properly escaped and validated before being used in an SQL query, which helps prevent SQL injection attacks.
2nd PHP Example of Preventing SQL Injections:
Another example of a PHP script that prevents SQL injection using prepared statements and parameterized queries
<?php
// Connect to the database using PDO
$db = new PDO('mysql:host=localhost;dbname=mydatabase', 'myusername', 'mypassword');
// Prepare the SQL statement with placeholders for the parameters
$stmt = $db->prepare("SELECT * FROM users WHERE username = ? AND password = ?");
// Set the parameter values from user input (in this case, from a form submission)
$username = $_POST['username'];
$password = $_POST['password'];
// Execute the statement with the parameter values
$stmt->execute([$username, $password]);
// Fetch the results
$results = $stmt->fetchAll();
// Do something with the results (in this case, just print them out)
print_r($results);
?>In this example, we’re again using PDO to connect to a MySQL database. We then use the prepare() method to create a prepared statement with placeholders for the parameters we’ll be using. However, instead of using named placeholders like in the previous example, we’re using question marks (?) as placeholders.
We then use the execute() method to execute the statement with an array of parameter values. The values are bound to the placeholders in the order they appear in the SQL statement.
Using prepared statements and parameterized queries like this helps prevent SQL injection attacks by ensuring that any user input is properly escaped and validated before being used in an SQL query.
PHP code example that demonstrates how to prevent cross-site scripting (XSS) attacks by sanitizing user input:
<?php
// Define a function to sanitize user input
function sanitizeInput($input) {
$sanitizedInput = strip_tags($input); // Remove any HTML tags
$sanitizedInput = htmlspecialchars($sanitizedInput, ENT_QUOTES, 'UTF-8'); // Convert special characters to HTML entities
return $sanitizedInput;
}
// Example usage
$userInput = $_POST['input_field'];
$sanitizedInput = sanitizeInput($userInput);
// Use the sanitized input in your application
echo "Your input was: " . $sanitizedInput;
?>In this code example, the sanitizeInput function takes user input and removes any HTML tags and converts special characters to HTML entities using the strip_tags and htmlspecialchars functions, respectively. This helps prevent attackers from injecting malicious code into your application through user input. The sanitized input is then used in the application, in this case, printed to the screen.
It’s important to note that this code example is just one way to prevent XSS attacks and should be used in conjunction with other security measures, such as input validation and output encoding, to provide comprehensive protection against data breaches.
PHP code example that demonstrates how to protect against data breaches through APIs using secure authentication methods:
<?php
// Set up the API credentials
$apiKey = 'your_api_key';
$apiSecret = 'your_api_secret';
// Define a function to generate the authentication token
function generateAuthToken($apiKey, $apiSecret) {
$timestamp = time(); // Get the current UNIX timestamp
$nonce = md5(uniqid(mt_rand(), true)); // Generate a unique nonce
$authString = $apiKey . $timestamp . $nonce; // Concatenate the API key, timestamp, and nonce
$authToken = hash_hmac('sha256', $authString, $apiSecret); // Generate the authentication token using the HMAC-SHA256 algorithm
return array('Authorization: ' . $authString . ':' . $authToken, 'Timestamp: ' . $timestamp, 'Nonce: ' . $nonce); // Return the authentication headers
}
// Example API request
$url = 'https://api.example.com/v1/users';
$method = 'POST';
$data = array('username' => 'johndoe', 'password' => 'pa$$word123');
// Generate the authentication headers
$authHeaders = generateAuthToken($apiKey, $apiSecret);
// Set up the cURL request
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_CUSTOMREQUEST, $method);
curl_setopt($ch, CURLOPT_POSTFIELDS, http_build_query($data));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);
curl_setopt($ch, CURLOPT_HTTPHEADER, $authHeaders);
// Execute the request
$response = curl_exec($ch);
curl_close($ch);
// Process the response
if ($response === false) {
echo 'API request failed';
} else {
$responseData = json_decode($response, true);
echo 'API response: ' . print_r($responseData, true);
}
?>In this code example, we set up the API credentials ($apiKey and $apiSecret) and define a function generateAuthToken that generates an authentication token using the HMAC-SHA256 algorithm. The authentication headers ($authHeaders) are then passed to the cURL request using the CURLOPT_HTTPHEADER option.
By using secure authentication methods like HMAC-SHA256, we can help prevent unauthorized access to our APIs and protect against data breaches. It’s important to note that this code example is just one way to protect against data breaches through APIs and should be used in conjunction with other security measures, such as rate limiting and input validation, to provide comprehensive protection against attacks.
Conclusion: Data breaches are a growing concern for individuals, organizations, and governments worldwide. They are caused by a combination of technical vulnerabilities, human errors, and malicious attacks, and can have severe consequences, including financial losses, reputational damage, and legal liabilities. To prevent data breaches, organizations should implement comprehensive security measures, including encryption, firewalls, access controls, and employee training programs. The study highlights coding examples of how data breaches can occur, and recommends that developers should use secure coding practices to prevent vulnerabilities that can be exploited by hackers. In conclusion, preventing data breaches requires a multi-faceted approach, where individuals, organizations, and governments work together to mitigate the risks of cyber attacks and protect sensitive information.