In cybersecurity, the concept of honeypots has emerged as a fascinating strategy to detect, analyze, and mitigate potential threats malicious actors pose. A honeypot refers to a deceptive system or network resource that is designed to attract and deceive attackers, allowing cybersecurity professionals to gain insights into their tactics, techniques, and motivations. This essay aims to explore the concept of honeypots, and their purpose, and provide examples of honeypot scripts such as SSH and FTP, elucidating their functionality and how they contribute to strengthening cybersecurity defenses.
Understanding Honeypots:
A honeypot is essentially a trap set by cybersecurity professionals to attract and monitor unauthorized access attempts and cyber-attacks. By mimicking genuine systems, honeypots create an environment that appears appealing to potential attackers, luring them into interacting with deceptive resources rather than actual critical systems. These decoy systems serve multiple purposes, including collecting valuable information about attackers’ methodologies, identifying new threats, and diverting malicious activities from legitimate targets.
Honeypot Scripts and Their Functionality:
SSH Honeypot:
An SSH honeypot is designed to mimic a Secure Shell (SSH) server, an essential network protocol used for secure remote access to systems. The SSH honeypot script emulates the functionalities of a genuine SSH server, allowing attackers to connect and interact with it. As attackers attempt to log in or exploit vulnerabilities, the honeypot captures their activities, providing valuable insights into the techniques they employ, such as brute-force attacks or the use of specific exploit scripts. This information helps security professionals understand emerging threats, improve security measures, and develop effective countermeasures.
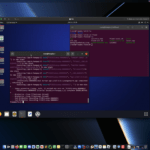
I have created various SSH Honeypot scripts such as this one HERE.
This SSH honeypot script was written in C++ and designed to troll the attacker and counter-attack them. It also detects open ports of the attacker and shows their location.
FTP Honeypot:
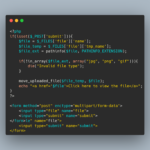
File Transfer Protocol (FTP) honeypots simulate FTP servers, a protocol primarily used for transferring files over a network. By presenting a seemingly legitimate FTP server, security experts can observe and analyze attackers’ actions when they attempt unauthorized access or transfer of malicious files. The FTP honeypot script records the attacker’s IP addresses, credentials used, file transfers, and commands executed. These details enable cybersecurity professionals to understand attack patterns, identify new malware or intrusion techniques, and bolster defense mechanisms accordingly.
Similar to my SSH honeypot script, I am working on a similar FTP Honeypot script that also counterattacks the attacker.
Web Honeypots:
Web honeypots are designed to mimic vulnerable web applications or websites. These honeypots can be created using scripts that emulate known vulnerabilities, such as SQL injection or cross-site scripting (XSS). When attackers target these vulnerable web honeypots, they unknowingly reveal their techniques and intentions. By analyzing the attacker’s actions, security experts can develop effective countermeasures, patch vulnerabilities, and enhance overall web application
security.
Benefits and Limitations of Honeypots:
Honeypots offer several benefits to organizations and security professionals. They provide an invaluable source of information, offering insights into new attack vectors, emerging threats, and hacker motivations. Honeypots also serve as an early warning system, alerting security teams to potential breaches and allowing for swift response and mitigation. Additionally, they divert attackers’ attention away from genuine systems, minimizing the risk of damage to critical infrastructure.
However, honeypots also come with certain limitations. They require careful planning, deployment, and monitoring to ensure they remain effective and do not inadvertently expose sensitive data. There is also a risk of attackers discovering honeypots, potentially leading to retaliatory actions or the use of the honeypot itself as a launching pad for further attacks. Thus, organizations must weigh the benefits against the potential risks before implementing honeypot strategies.
Honeypots offer a compelling approach to cybersecurity by attracting and deceiving attackers, providing valuable insights into their methodologies. Scripts mimicking protocols like SSH, FTP