Note: I have a lot of security scripts and demo in my GitHub (https://github.com/lynxgeeknyc)
Web application security is a major concern for businesses and individuals who rely on online services. Attackers are continuously finding new ways to exploit vulnerabilities in web applications to gain access to sensitive data or take control of systems. Three common types of web application attacks are Server-Side Request Forgery (SSRF), Server-Side Template Injection (SSTI), and Web Shell Attacks. In this essay, we will discuss these three types of attacks, their consequences, and best practices for prevention.
Server-Side Request Forgery (SSRF) is an attack that targets the server by sending a forged request from the server to other internal or external servers. The attacker can use this attack to make the server perform actions that it wasn’t intended to do, such as requesting sensitive data or launching an attack on another server. This attack can be especially dangerous if the attacker gains access to the server’s local network.
To prevent SSRF attacks, developers should validate all user input and sanitize any data before sending it to the server. Additionally, they should implement access control measures to limit the server’s access to external resources. Below is an example of a vulnerable code that can be used to exploit SSRF:
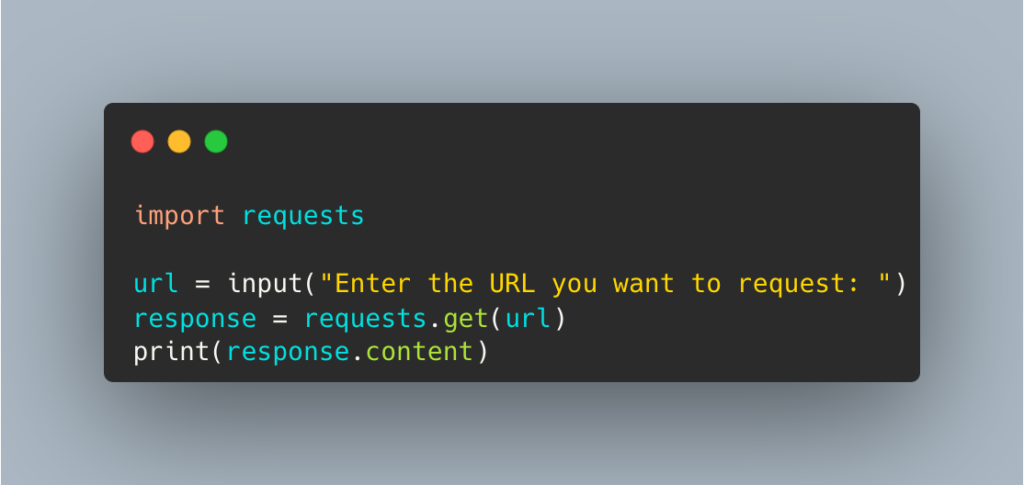
In the above code, the user can enter any URL they want, including internal server addresses, making it vulnerable to SSRF attacks. To prevent this, developers can use the following code:
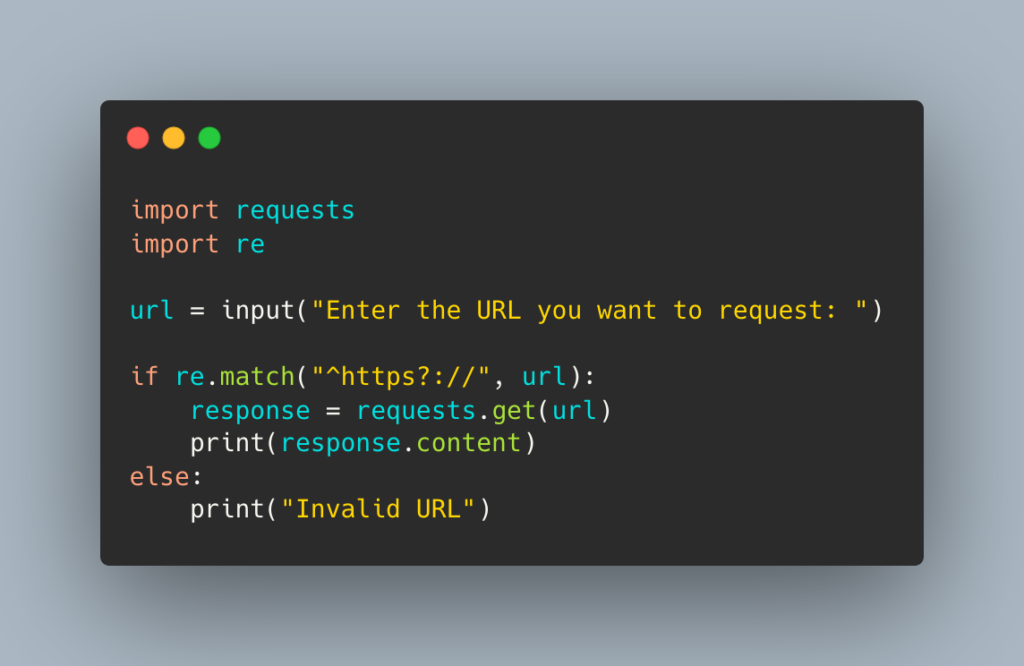
The updated code uses regular expressions to validate the URL and only allows HTTP and HTTPS requests.
Server-Side Template Injection (SSTI) is an attack that targets web applications that use templates to generate dynamic content. The attacker injects malicious code into the template, which is executed on the server-side. This can lead to sensitive data being leaked or the server being compromised.
To prevent SSTI attacks, developers should sanitize all user input and use secure template engines that prevent code injection. Below is an example of a vulnerable code that can be used to exploit SSTI:
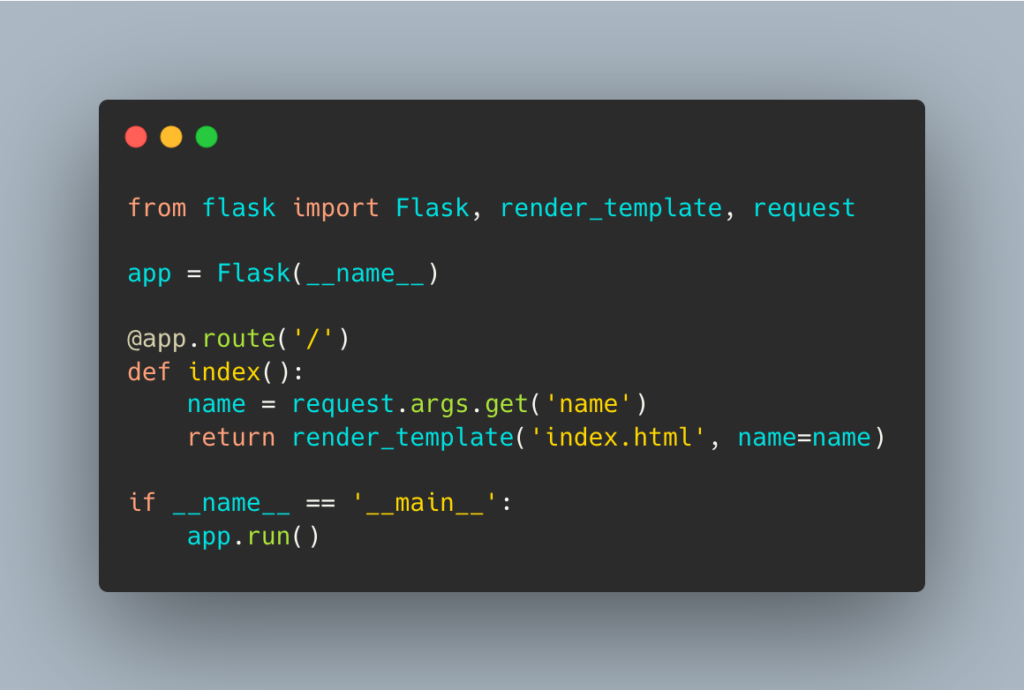
In the above code, the user can enter any value for the “name” parameter, including malicious code. To prevent SSTI attacks, developers can use the following code:
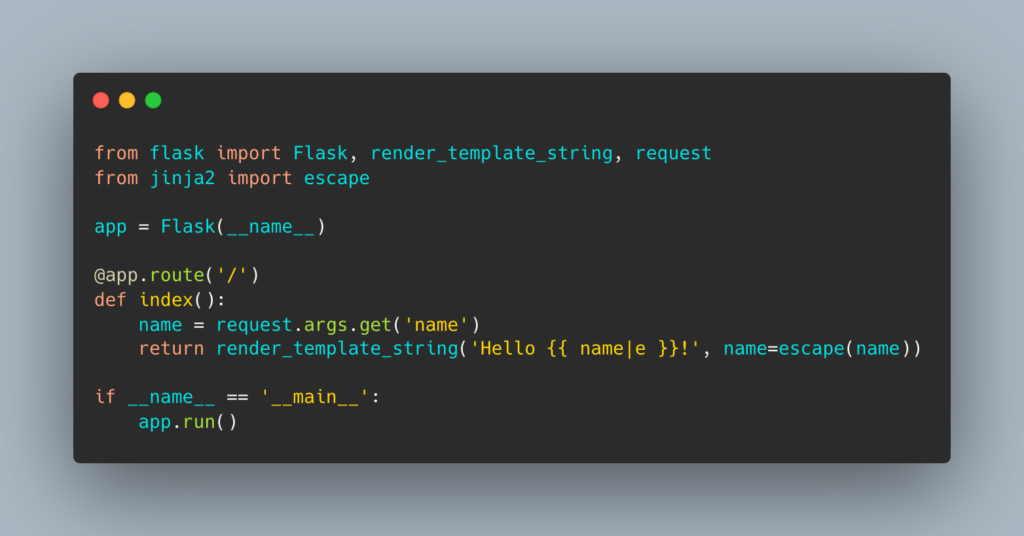
The updated code uses the Jinja2 template engine, which automatically escapes any user input to prevent code injection.
Web Shell Attacks are a type of attack where the attacker gains access to a server by uploading a script that allows them to execute commands on the server. This can lead to sensitive data being stolen, systems being compromised, or the server being used to launch attacks on other systems.
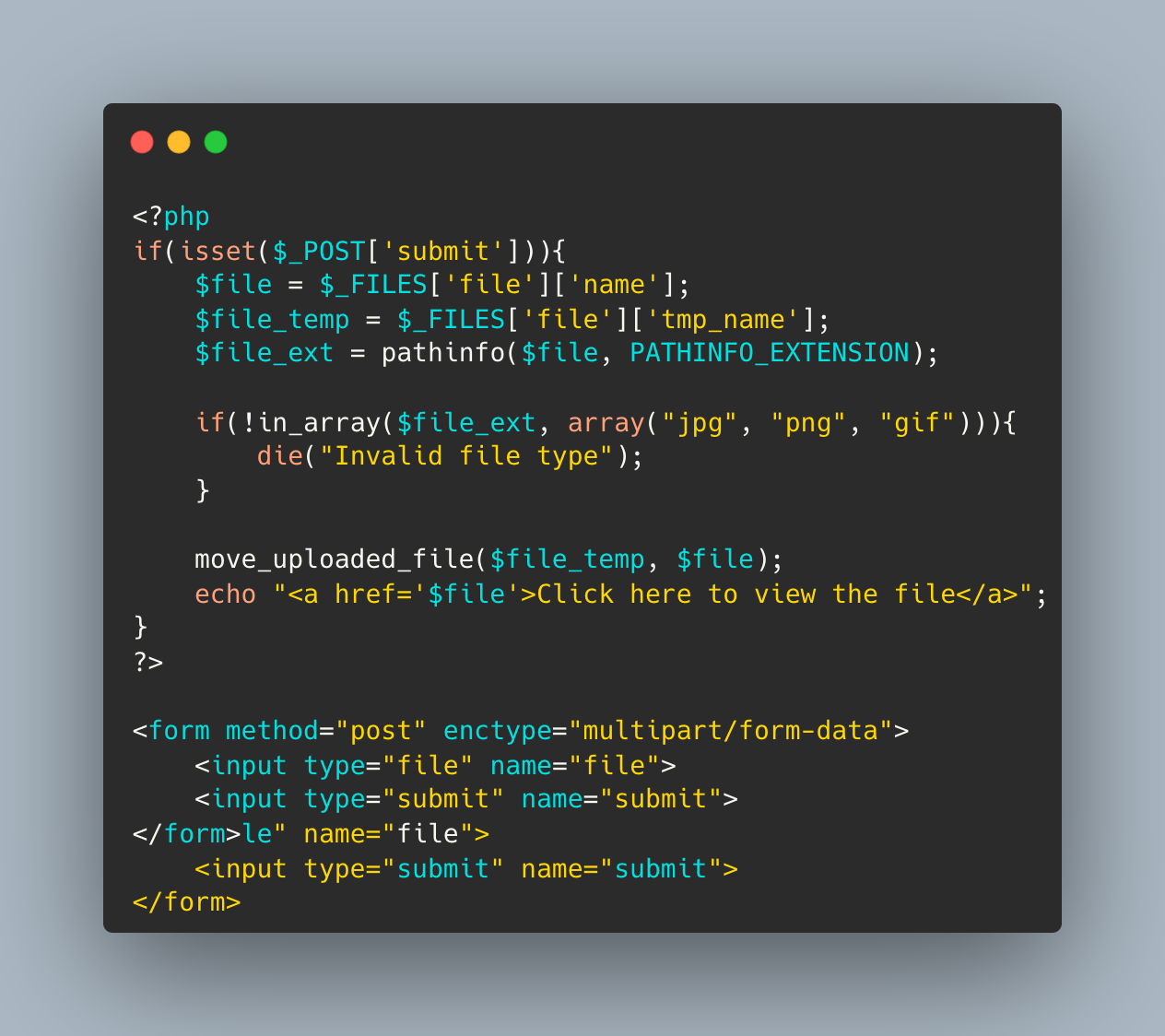
To prevent web shell attacks, developers should validate all user input and limit the server’s file upload capabilities. Additionally, they should monitor the server for any suspicious activity. Below is an example of a vulnerable code that can be used to exploit web shell attacks:
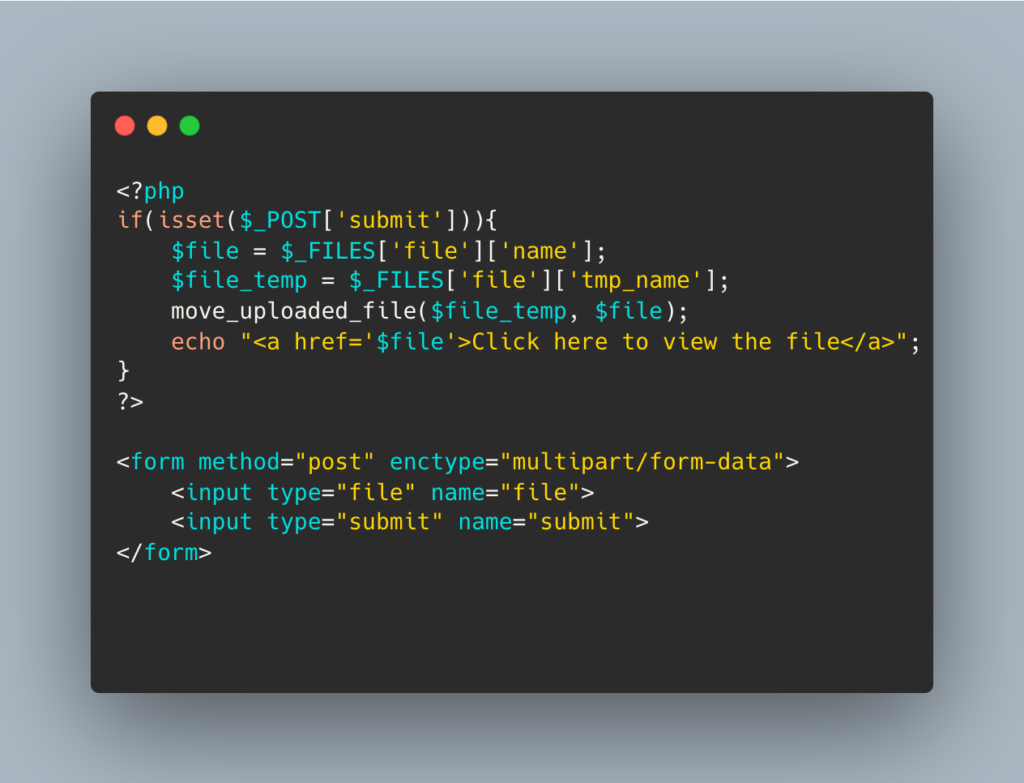
In the above code, the attacker can upload a script file that allows them to execute commands on the server. To prevent web shell attacks, developers can use the following code:
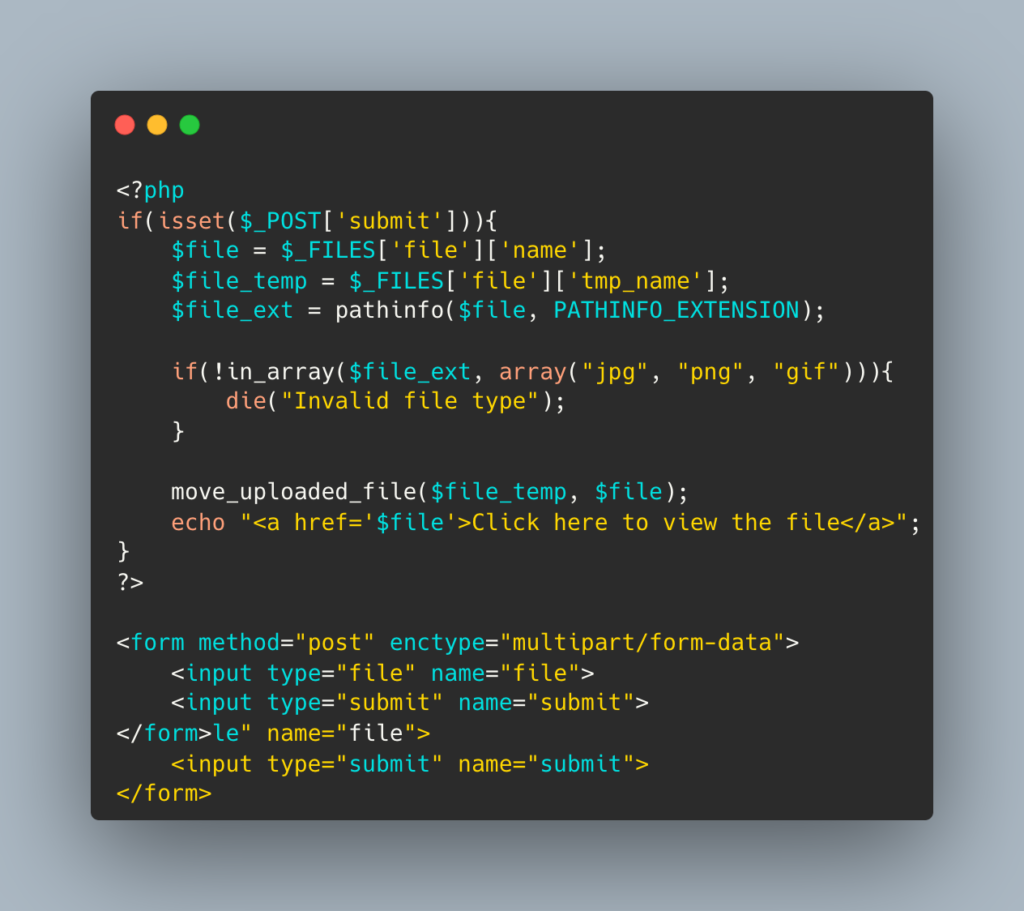
The updated code only allows the user to upload image files and checks the file extension before allowing it to be uploaded.